當我們在登錄像QQ郵箱這種大多數的網站,往往在登錄按鍵上會有下次自動登錄這個選項,勾選后登錄成功,在一段時間內,即便退出瀏覽器或者服務器重啟,再次訪問不需要用戶輸入賬號密碼進行登錄,這也解決了用戶每次輸入賬號密碼的麻煩。

接下來實現自動登陸。
applicatio.properties配置用戶名密碼
spring.security.user.name=java spring.security.user.password=java
controller層實現
@RestController
public class HelloController {
@GetMapping("/hello")
public String hello() {
return "hello";
}
}
配置類實現
@Configuration public class SecurityConfig extends WebSecurityConfigurerAdapter { @Override protected void configure(HttpSecurity http) throws Exception { http.formLogin() .and() .authorizeRequests() .anyRequest() .authenticated() .and() .rememberMe() .and() .csrf().disable(); }
訪問http://localhost:8080/hello,此時系統會重定向到登錄頁面。

二話不說,輸入賬號密碼,開搞!
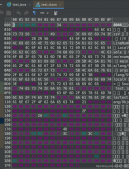
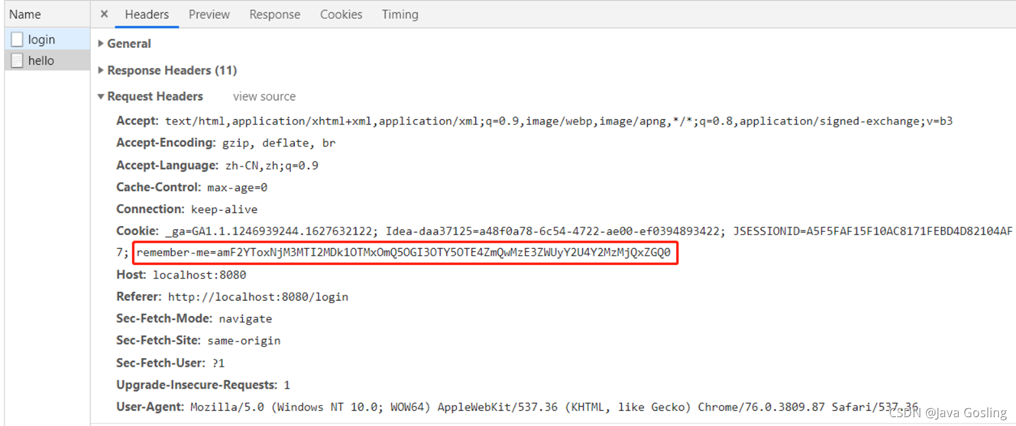
此時看到了登錄數據remember-me的值為on,當自定義登陸框的時候應該知道如何定義key了吧。

在hello接口,可以很清楚的看到cookie里保存了一個remember-me的令牌,這個就是自動登錄的關鍵所在。
至于令牌是怎么生成的,先看一段源碼。核心處理類TokenBasedRememberMeServices->onLoginSuccess
public void onLoginSuccess(HttpServletRequest request, HttpServletResponse response, Authentication successfulAuthentication) {
//拿到用戶名和密碼
String username = this.retrieveUserName(successfulAuthentication);
String password = this.retrievePassword(successfulAuthentication);
//用戶名為空 打印日志
if (!StringUtils.hasLength(username)) {
this.logger.debug("Unable to retrieve username");
} else {
//密碼為空 通過用戶名再去查詢
if (!StringUtils.hasLength(password)) {
UserDetails user = this.getUserDetailsService().loadUserByUsername(username);
password = user.getPassword();
//查到的密碼還為空 打印日志 結束
if (!StringUtils.hasLength(password)) {
this.logger.debug("Unable to obtain password for user: " + username);
return;
}
}
//令牌有效期的生成 1209600是兩周 也就是說令牌有效期14天
int tokenLifetime = this.calculateLoginLifetime(request, successfulAuthentication);
long expiryTime = System.currentTimeMillis();
expiryTime += 1000L * (long)(tokenLifetime < 0 ? 1209600 : tokenLifetime);
//生成簽名 signature
String signatureValue = this.makeTokenSignature(expiryTime, username, password);
//設置cookie
this.setCookie(new String[]{username, Long.toString(expiryTime), signatureValue}, tokenLifetime, request, response);
if (this.logger.isDebugEnabled()) {
this.logger.debug("Added remember-me cookie for user "" + username + "", expiry: "" + new Date(expiryTime) + """);
}
}
}
//使用MD5加密 通過用戶名、令牌有效期、密碼和key生成rememberMe的令牌 這里的key也就是加密的鹽值
protected String makeTokenSignature(long tokenExpiryTime, String username, String password) {
String data = username + ":" + tokenExpiryTime + ":" + password + ":" + this.getKey();
try {
MessageDigest digest = MessageDigest.getInstance("MD5");
return new String(Hex.encode(digest.digest(data.getBytes())));
} catch (NoSuchAlgorithmException var7) {
throw new IllegalStateException("No MD5 algorithm available!");
}
}
看完了核心的源碼,也就知道了令牌的生成規則:username + “:” + tokenExpiryTime + “:” + password + “:” + key(key 是一個散列鹽值,可以用來防治令牌被修改,通過MD5散列函數生成。),然后通過Base64編碼。
取出剛才的remember-me=amF2YToxNjM3MTI2MDk1OTMxOmQ5OGI3OTY5OTE4ZmQwMzE3ZWUyY2U4Y2MzMjQxZGQ0進行下驗證。

解碼后是java:1637126095931:d98b7969918fd0317ee2ce8cc3241dd4,很明顯java是username,1637126095931是兩周后的tokenExpiryTime,d98b7969918fd0317ee2ce8cc3241dd4是password和key值的MD5加密生成的。
需要注意的是key值是通過UUID隨機生成的,當重啟服務器時,UUID的變化會導致自動登錄失敗,所以為了避免之前生成的令牌失效,可以在配置中定義key值。
@Override
protected void configure(HttpSecurity http) throws Exception {
http.formLogin()
.and()
.authorizeRequests()
.anyRequest()
.authenticated()
.and()
.rememberMe()
.key("HelloWorld")
.and()
.csrf().disable();
}
在Spring Security―登陸流程分析曾經說到 Spring Security中的認證授權都是通過過濾器來實現的。RememberMeAuthenticationFilter 是自動登錄的核心過濾器。
public class RememberMeAuthenticationFilter extends GenericFilterBean implements ApplicationEventPublisherAware {
private void doFilter(HttpServletRequest request, HttpServletResponse response, FilterChain chain)
throws IOException, ServletException {
//獲取當前用戶實例 繼續過濾校驗
if (SecurityContextHolder.getContext().getAuthentication() != null) {
this.logger.debug(LogMessage
.of(() -> "SecurityContextHolder not populated with remember-me token, as it already contained: ""
+ SecurityContextHolder.getContext().getAuthentication() + """));
chain.doFilter(request, response);
return;
}
//登錄獲取Auth
Authentication rememberMeAuth = this.rememberMeServices.autoLogin(request, response);
if (rememberMeAuth != null) {
// Attempt authenticaton via AuthenticationManager
try {
//進行remember-me校驗
rememberMeAuth = this.authenticationManager.authenticate(rememberMeAuth);
// Store to SecurityContextHolder
//保存用戶實例
SecurityContextHolder.getContext().setAuthentication(rememberMeAuth);
//成功頁面跳轉
onSuccessfulAuthentication(request, response, rememberMeAuth);
this.logger.debug(LogMessage.of(() -> "SecurityContextHolder populated with remember-me token: ""
+ SecurityContextHolder.getContext().getAuthentication() + """));
if (this.eventPublisher != null) {
this.eventPublisher.publishEvent(new InteractiveAuthenticationSuccessEvent(
SecurityContextHolder.getContext().getAuthentication(), this.getClass()));
}
if (this.successHandler != null) {
this.successHandler.onAuthenticationSuccess(request, response, rememberMeAuth);
return;
}
}
catch (AuthenticationException ex) {
this.logger.debug(LogMessage
.format("SecurityContextHolder not populated with remember-me token, as AuthenticationManager "
+ "rejected Authentication returned by RememberMeServices: "%s"; "
+ "invalidating remember-me token", rememberMeAuth),
ex);
this.rememberMeServices.loginFail(request, response);
//失敗頁面跳轉
onUnsuccessfulAuthentication(request, response, ex);
}
}
chain.doFilter(request, response);
}
}
@Override
public final Authentication autoLogin(HttpServletRequest request, HttpServletResponse response) {
//獲取cookie
String rememberMeCookie = extractRememberMeCookie(request);
if (rememberMeCookie == null) {
return null;
}
this.logger.debug("Remember-me cookie detected");
if (rememberMeCookie.length() == 0) {
this.logger.debug("Cookie was empty");
cancelCookie(request, response);
return null;
}
try {
//解碼cookie 拿到令牌
String[] cookieTokens = decodeCookie(rememberMeCookie);
//通過令牌獲取UserdDetails
UserDetails user = processAutoLoginCookie(cookieTokens, request, response);
this.userDetailsChecker.check(user);
this.logger.debug("Remember-me cookie accepted");
return createSuccessfulAuthentication(request, user);
}
catch (CookieTheftException ex) {
cancelCookie(request, response);
throw ex;
}
catch (UsernameNotFoundException ex) {
this.logger.debug("Remember-me login was valid but corresponding user not found.", ex);
}
catch (InvalidCookieException ex) {
this.logger.debug("Invalid remember-me cookie: " + ex.getMessage());
}
catch (AccountStatusException ex) {
this.logger.debug("Invalid UserDetails: " + ex.getMessage());
}
catch (RememberMeAuthenticationException ex) {
this.logger.debug(ex.getMessage());
}
cancelCookie(request, response);
return null;
}
大致整體流程就是如果拿不到實例,則進行remember-me驗證,通過autoLogin方法里獲取cookie,解析令牌,拿到Auth,最后進行校驗。之后剩下的和登陸流程分析的差不多。
到此這篇關于Spring Security實現自動登陸功能示例的文章就介紹到這了,更多相關Spring Security 自動登陸內容請搜索服務器之家以前的文章或繼續瀏覽下面的相關文章希望大家以后多多支持服務器之家!
原文鏈接:https://blog.csdn.net/MAKEJAVAMAN/article/details/121128043